Hacker-proof Your Website with These Proven Techniques
Hackers. They are wise and wild kind. They manage to find some loophole or backdoor in a system and steal their way into innocent websites. Once inside, they inject and infect the website with malware, spyware or steal sensitive files that will kill the website and its credibility. If it is an online store, the business is almost closed.
Sounds terrifying, right? Most website owners are prone to getting their websites hacked because: i) they either lack to knowledge to shield their websites, or ii) they do not invest in proper security mechanisms that can thwart such attacks.
Whatever the case maybe, you do not want to be forming part of the ignorant group that let their websites taken over by hackers. So, we thought of putting together these proven techniques that some of the world-class websites have been deploying to hacker-proof themselves.
Update everything
Do you know millions of devices got affected by the recent WannaCry ransomware? All the affected systems were not updated with the security patch that Microsoft has been releasing periodically.
Software updates and security patches are sent by software vendors to ensure that existing security lapses and performance issues are rectified to make the software idea for use. Missing to update them is a surefire way to invite hackers right into your system.
Keep the software, CMS, scripts, themes, and extensions used in your website up-to- date to stay hacker-proof. Secondly, check if the website has any underlying weakness that can possibly facilitate a hack. If you any find any, which is possible with the help of malware scanners and vulnerability assessment systems, remove them right away.
Set up minimal password controls
Avoid using commonly used passwords since hackers attempt brute force attacks with commonly used passwords. A quick list of commonly used passwords is below:
Create passwords with adequate length, width and depth. As a rule, keep passwords that include:
- uppercase letters: A, B, C;
- numerals such: 1, 2, 3;
- lowercase letters: a, b,c;
- special characters such as !, @, #; %, etc.
This will make the password too complex to guess. Further, users and admins should be instructed to refrain from writing down the password. There should be no visible record of the password, lest it can be easily stolen. Hackers can easily get hold of passwords through shoulder-surfing and dumpster diving.
Migrate to HTTPS
If you are a regular user of the the web, specifically online stores, you must have noticed a green address bar with a padlock symbol on most sites.
HTTPS has become a standard protocol on the Internet today. It not only secures the web for the user but also ensures that any sensitive information, like credit card numbers, login credentials, etc. are safely exchanged between the user and the website’s server.
HTTPS can be setup by configuring the website with SSL certificates. There are several alternatives available in the market like GeoTrust SSL Certificates, Symantec, VeriSign, etc. all of which are good choices to consider. You can pick from annual or bi-annual certificate plans as per requirements.
Secure directory
You can protect your directory by creating a .htpasswd file and uploading it to a safe location in the website server. Once it is uploaded, ensure that the .htaccess file is pointed correctly towards the password file. Now upload the .htaccess file into the directory and do a double-check to ensure that the password security is working.
File permissions
File permissions do the basic task of specifying who can read, write, modify or access what kind of data stored on the website. Missing to set file permissions is the easiest way to let hackers get into your website and change stuff as they wish or simply steal them. If your website is hosted on a Linux server, you can find settings to set file permissions under cPanel -> Files > File Manager.
Third-party assistance
Cyber-security is a dynamically evolving domain. No single website owner can stay tuned to the rapid changes and innovative strategies that hackers adopt to break into innocent systems. However, putting the shield down is not an option either.
In such cases, it would be ideal to seek third-party assistance. Third-party security vendors can monitor the website performance, security vulnerabilities, malware penetration and similar threats for a periodical fee or on a subscription basis. Sucuri, SiteLock, Qualys are some such examples.
Use website security tools
If paying for a third-party security expert is not your choice, then you can consider investing in website security tools which do more or less the same thing. There are premium website security tools to pick from that implement all kinds of security measures for your website, including XSS scripting, malware scanning, vulnerabilities assessment, etc. Netsparker, SecurityHeaders, OpenVAS, etc. are some worthy choices.
Closing In
Cyber security is a matter of serious concern. No website owner can take his website security for granted, lest lose the website and perhaps the total control over it. Given the pace at which hackers at improving their ‘digital terrorism’ skills, it is mandatory that you, as a website owner, invests time and money in resources that would ensure total security for your website. We have explained some such commonly resorted techniques and systems above in this article.
Got any doubts? Have any further ideas that can improve a website’s security quotient? Let us know.
Author Bio
This article has been published by Ajit Dash. He is the founder of TechTrickPoint, enthusiastic about Online Marketing. He loves to develop Digital Marketing and and social media entrepreneur Plans also.
Follow Ajit Dash: Google Plus Twitter







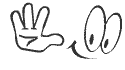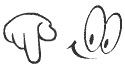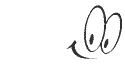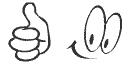







Leave a Reply